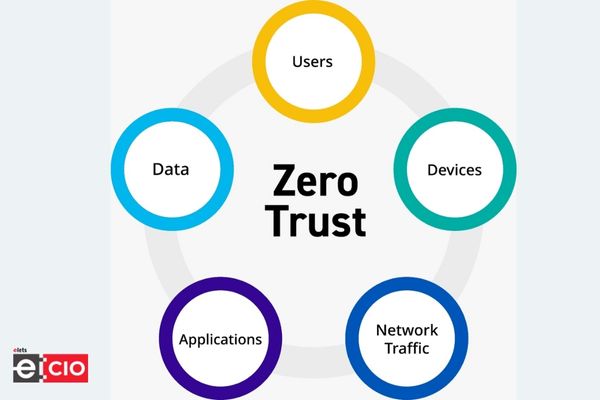
As security concerns continue to mount, more and more enterprises are turning to zero-trust security models. This approach treats all network traffic as untrusted, regardless of source or destination. All traffic is encrypted and verified before being allowed to enter the network.
The Zero Trust model is well-suited to today’s remote work Employees accessing corporate data from a variety of devices, making it more important than ever to ensure that all traffic is secure.

As businesses seek ways to protect their data from increasingly sophisticated cyber threats, zero trust security is gaining traction in India. Zero trust security can assist Indian enterprises in keeping their data secure by encrypting all traffic and verifying its authenticity.
Zero Trust architecture critical for 5G networks
The Zero Trust approach will become even more critical as 5G networks are rolled out, which will provide higher speeds and greater connectivity.5 will enable a new era of mobile connectivity, with faster speeds and lower latency. This will open up new business opportunities and create new security challenges. 5G networks will be more complex than previous generations, making them more vulnerable to attack.

Zero trust security models can help enterprises secure their 5G networks by encrypting all traffic and verifying its authenticity. This will ensure that only authorised users can access corporate data and that all traffic is safe from malicious attacks.
Conclusion
Cybersecurity is a major concern for businesses of all sizes. The number of cyberattacks is intensifying, and the cost of data breaches is rising. Preventing insider threats is one of the most difficult challenges in cybersecurity. Insider threats pose a significant security risk because they have access to sensitive information and systems. They may also be able to evade traditional security measures. Employees and even malicious insiders can pose insider threats.
Finally, Zero trust architecture is one approach that can help organisations mitigate insider threats. Zero trust provides strict authentication and authorization controls for all users, regardless of their location or device. This type of architecture can help organizations better protect their data and systems from malicious insiders.











